Hello,
i have installed openEDR agent in windows endpoint and parsed the openEDR logs inside elk using filebeat and logstash plugin. Below are the fields.
_id: Unique identifier for the log entry._index: Index name where the log entry is stored._score: Score of the log entry (typically used in search results).@timestamp: Timestamp of when the log entry was recorded.@version: Version of the log entry.agent.ephemeral_id: Ephemeral identifier for the agent responsible for collecting the log entry.agent.id: Identifier for the agent responsible for collecting the log entry.agent.name: Name of the agent responsible for collecting the log entry.agent.type: Type of agent responsible for collecting the log entry.agent.version: Version of the agent responsible for collecting the log entry.ecs.version: Version of the ECS (Elastic Common Schema) used.event.original: The original event data before parsing.host.architecture: Architecture of the host system.host.hostname: Hostname of the system where the event occurred.host.id: Unique identifier for the host system.host.ip: IP addresses associated with the host system.host.mac: MAC address of the host system.host.name: Name of the host system.host.os.build: Build version of the operating system.host.os.family: Family of the operating system (e.g., Windows).host.os.kernel: Kernel version of the operating system.host.os.name: Name of the operating system.host.os.platform: Platform of the operating system (e.g., Windows).host.os.type: Type of operating system (e.g., Windows).host.os.version: Version of the operating system.input.type: Type of input used to collect the log entry.log.file.idxhi: High index of the log file.log.file.idxlo: Low index of the log file.log.file.path: Path of the log file.log.file.vol: Volume of the log file.log.offset: Offset within the log file where the entry was read.parsed_json.baseEventType: Base event type.parsed_json.baseType: Base type.parsed_json.childProcess.*: Information about child processes.parsed_json.customerId: Customer ID.parsed_json.deviceName: Name of the device.parsed_json.endpointId: Endpoint ID.parsed_json.processes.*: Information about processes.parsed_json.sessionUser: User associated with the session.parsed_json.time: Time associated with the parsed JSON.parsed_json.type: Type of parsed JSON.parsed_json.version: Version of parsed JSON.tags: Additional tags applied to the log entry.
these many fields i’m able to see in discover of openEDR logs
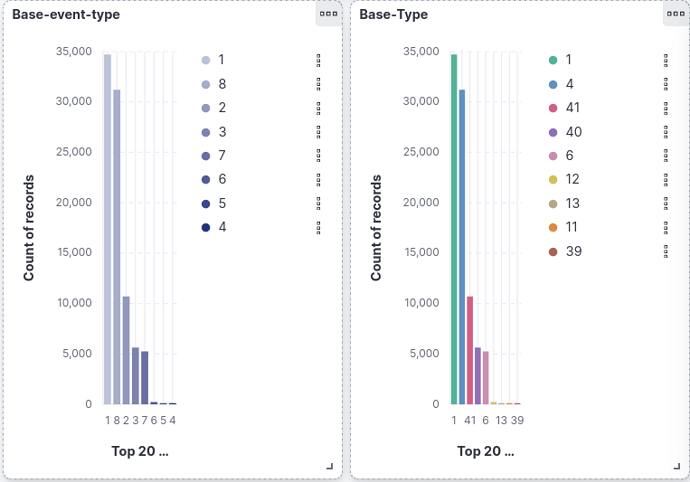
i have created a dashboard for these fields but it was not informative because
here it showing the base event and base in number how could we know that what it define. I also searched about those i’m not getting any information about that numbers.
as it showing the file path how can i detect the malware from it
please suggest!!! fast ![]()